Bilirkişilerin Uyacağı Rehber İlkeler ve Bilirkişi Raporlarında Bulunması Gereken Standartlar
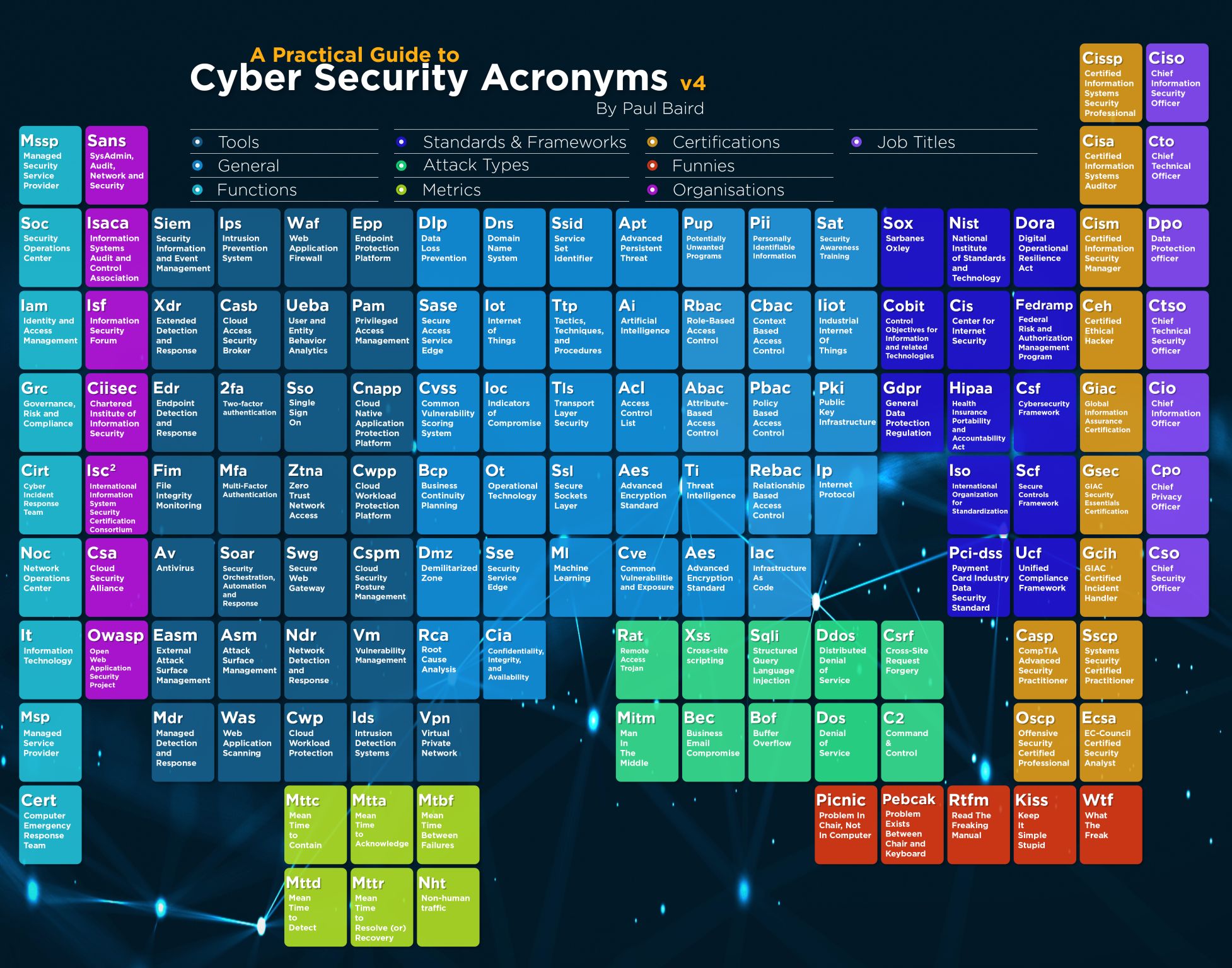
ECE R155, Birleşmiş Milletler Avrupa Ekonomik Komisyonu'nun (ECE) 155 Sayılı Yönetmeliğidir. Bu yönetmelik, araçların siber güvenlik ve siber güvenlik yönetim sistemleri açısından onaylanması ilişkin yeknesak hükümleri ortaya koyar. Ayrıca metnin içinde Otomotiv Siber saldırı tehditleri ve yöntemleri ile bunlara karşı alınabilecek önlemler belirtilmiştir. Türkçe tam metin için bizimle irtibata geçin.
Otomotiv Siber Saldırı ve Güvenlik Açıkları Listesi. Kaynak ECE R 155
Ses ve Görüntü Uzmanı Cemal Emre Doğan tarafından hazırlanan Deepfake(Derin Sahtecilik) nasıl anlaşılır çalışması.
ECE R155, Birleşmiş Milletler Avrupa Ekonomik Komisyonu'nun (ECE) 155 Sayılı Yönetmeliğini ifade eder. Bu yönetmelik, araçların siber güvenlik ve siber güvenlik yönetim sistemleri açısından onaylanmasına ilişkin yeknesak hükümleri ortaya koymaktadır. ECE R155, özellikle elektronik ve iletişim sistemlerine odaklanarak araçların siber güvenliğini sağlamaya yönelik gereklilikleri ve prosedürleri belirler. Yetkisiz erişim, veri manipülasyonu ve siber saldırılardan kaynaklanan potansiyel güvenlik tehlikeleri ile ilgili riskler de dahil olmak üzere, modern araçlardaki siber güvenlik tehditleriyle ilgili artan endişeleri gidermeyi amaçlamaktadır. Yönetmelik, araç üreticileri tarafından uygulanacak siber güvenlik yönetim sistemlerine (CSMS) ilişkin ilkeleri özetlemekte ve araç elektronik sistemleri ile iletişim arayüzlerinin güvenliğinin sağlanmasına yönelik teknik gereklilikleri belirlemektedir. Araçlar daha bağlantılı hale geldikçe ve elektronik sistemlere bağımlı hale geldikçe, ECE R155'e uyumluluk giderek daha önemli hale geliyor. ECE R155, araçların siber güvenliğini sağlamak ve siber güvenlik düzenlemelerinin farklı ülke ve bölgeler arasında uyumlaştırılmasını teşvik etmek için uluslararası bir standart olarak hizmet vermektedir. Tüketiciler için araçların emniyet ve güvenliğinin artırılmasına katkıda bulunmanın yanı sıra otomotiv endüstrisinin siber güvenlik zorluklarını çözme becerisine güven oluşturulmasına yardımcı olur. İngilizce Metin İçin: https://unece.org/transport/documents/2021/03/standards/un-regulation-no-155-cyber-security-and-cyber-security BM Düzenlemesi No. 156 - Otomotiv Yazılım güncelleme ve yazılım güncelleme yönetim sistemi İngilizce Metin İçin https://unece.org/transport/documents/2021/03/standards/un-regulation-no-156-software-update-and-software-update
ISO/SAE 21434:2021, Uluslararası Standardizasyon Örgütü (ISO) tarafından yayınlanan "Karayolu araçları – Siber güvenlik mühendisliği" başlıklı bir standarttır. Bu standart, otomotiv endüstrisinin araçlardaki elektrik ve elektronik sistemlerle ilgili siber güvenlik risklerini yönetmesine yönelik kılavuzlar ve öneriler sağlar. Araçların siber tehditlere karşı güvenliğinin sağlanmasına yönelik risk değerlendirmesi, siber güvenlik yönetimi, geliştirme süreçleri ve doğrulama yöntemleri gibi çeşitli hususları içerir. ISO 21434:2021, tasarım, geliştirme, üretim, işletme, bakım ve hizmetten çıkarma dahil olmak üzere otomotiv sistemlerinin yaşam döngüsü boyunca siber güvenlik mühendisliğine sistematik bir yaklaşım oluşturmayı amaçlamaktadır. Otomotiv endüstrisindeki üreticilerin, tedarikçilerin ve diğer paydaşların siber güvenlik önlemlerini süreçlerine ve ürünlerine etkin bir şekilde entegre etmelerine yardımcı olur. Standart, siber güvenliğin ürün geliştirmenin ilk aşamalarından itibaren ve bir aracın tüm yaşam döngüsü boyunca dikkate alınmasının önemini vurguluyor. Kuruluşlar, ISO 21434:2021'de belirtilen yönergeleri takip ederek otomotiv sistemlerinin siber saldırılara karşı dayanıklılığını artırabilir ve tüketiciler için araçların emniyetini ve güvenliğini sağlayabilir.

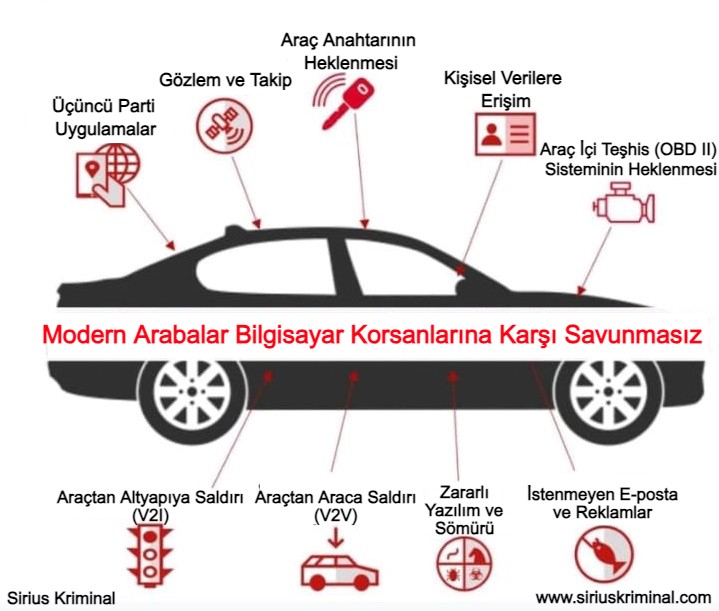
MODERN ARABALAR BİLGİSAYAR KORSANLARINA KARŞI KORUMASIZ
Mehmet ŞEN E. Emniyet Müdürü
Sirius Kriminal Kurucu Ortak
Bağlantı/Bağlanabilirlik ve Yazılım Tanımlı Mimarilerin entegrasyonu, Otomotiv ve Akıllı Mobil ekosisteminde devrim yaratarak; otonom sürüş, tahmine dayalı bakım ve gelişmiş bilgi-eğlence sistemleri gibi son teknoloji özellikleri mümkün kılmıştır. Ancak güncel ya da olası yenilikler bu ekosistemde önemli siber güvenlik sorunları da ortaya çıkarmıştır.
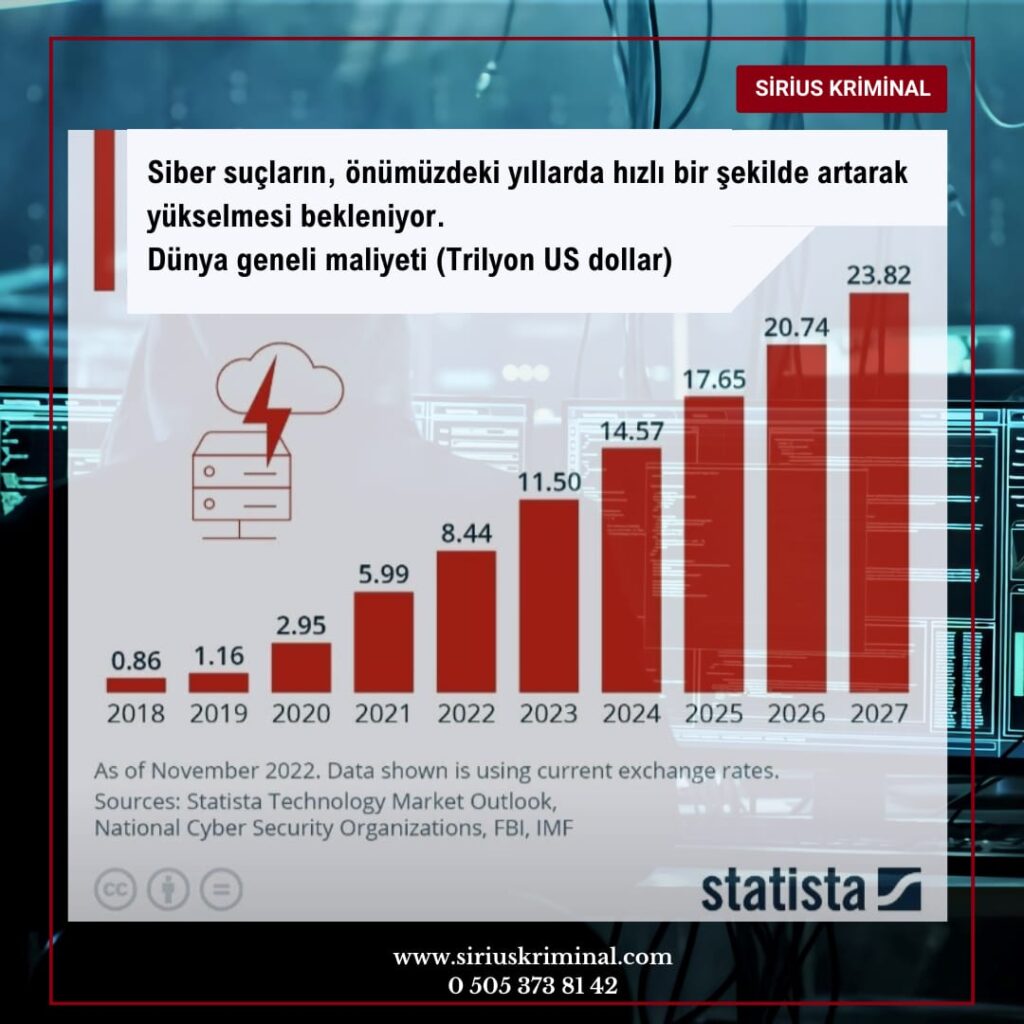
2023 yılı Otomotiv ve Mobil Siber Güvenlik ekosisteminde büyük ölçekli olaylara doğru dramatik bir değişime tanıklık etti. Upstream'in araştırmasına göre 2019-2023 yılları arasında, açık internette ifşa edilen olaylar yüzde 50 oranında artarak, 2023 yılında 295 raporlanan vakaya ulaşmıştır. 2023 yılında, yapılan saldırıların %95'i uzaktan ve %64'ü kötü niyetli (Siyah Şapkalı) bilgisayar korsanları tarafından gerçekleştirilmiştir.
Otomotiv siber saldırısı iki ana kategoriye ayrılabilir:
1- Uzaktan Saldırılar
a-Kısa menzilli (örn. ortadaki adam saldırısı) veya
b-Uzun menzilli (örn. API/Uygulama Programlama Arabirimi tabanlı saldırı)
2- Araca fiziksel bir bağlantı (örn. OBD/Araç İçi Teşhis Sistemi portu) gerektiren fiziksel saldırılar.
Uzaktan saldırılar ağ bağlantısına (örneğin Wi-Fi, Bluetooth, 3/4/5G ağları) dayanır ve çok sayıda aracı aynı anda etkileme potansiyeline sahiptir.
Otomotiv Siber Tehditleri, Temel Finansal Etkileri ve Araç Güvenliği
Uzaktan Araç Korsanlığı: Bilgisayar korsanları, bir aracın yazılımındaki veya iletişim protokollerindeki açıklardan yararlanarak elektronik kontrol ünitelerine (ECU'lar) yetkisiz erişim sağlayabilir ve frenler, direksiyon veya hızlanma gibi çeşitli sistemleri uzaktan manipüle edebilir. Bu durum potansiyel olarak kazalara veya araç hırsızlığına yol açabilir.
Anahtarsız Giriş ve Kontak Korsanlığı: Birçok modern araçta kablosuz sinyallere dayanan anahtarsız giriş ve ateşleme sistemleri kullanılmaktadır. Bilgisayar korsanları, anahtarsız giriş/marş motoru; röle; sinyal karıştırma ve API saldırı yöntemleri ile anahtara fiziksel erişim olmadan kapıların kilidini açmak, motoru çalıştırmak ve hatta aracı çalmak için bu sinyalleri kesebilir ve manipüle edebilir.
Bilgi-Eğlence Sistemi İstismarı: Bilgi-eğlence sistemleri genellikle Wi-Fi, Bluetooth veya hücresel bağlantılar gibi bağlantı özelliklerine sahiptir. Bilgisayar korsanları bu sistemlerdeki güvenlik açıklarından faydalanarak GPS konumları, arama kayıtları veya akıllı telefonlardan senkronize edilen kişisel bilgiler gibi araçta depolanan hassas verilere erişim sağlayabilir.
Konum takibi: Kullanıcı veya sahibinin izni olmadan bir aracın konumunu ve hareketini izlemek için GPS navigasyon verilerini kullanabilir.
Teşhis Portu İstismarı: Tamirciler tarafından araç arıza tespiti ve bakımı için kullanılan yerleşik arıza tespit (OBD-II) portu da bilgisayar korsanları tarafından istismar edilebilir. OBD-II portuna takılan kötü niyetli cihazlar potansiyel olarak aracın ağına erişim sağlayabilir ve kritik işlevleri kontrol edebilir.
Fidye Yazılımı Saldırıları: Siber suçlular fidye yazılımı saldırılarıyla otomotiv üreticilerini veya tedarikçilerini hedef alabilir, kritik sistemleri şifreleyebilir veya hassas verileri çalabilir ve bunların serbest bırakılması için ödeme talep edebilir. Bu durum üretim süreçlerini kesintiye uğratabilir veya müşteri verilerini tehlikeye atabilir.
Tedarik Zinciri Saldırıları: Otomotiv tedarik zincirleri, araç üretiminde kullanılan bileşenleri ve yazılımları sağlayan çok sayıda tedarikçiyi içerir. Bilgisayar korsanları bu tedarikçileri hedef alarak kötü amaçlı yazılımlar yerleştirebilir veya daha sonra araçlara entegre edilebilecek bileşenleri tehlikeye atarak önemli siber güvenlik riskleri oluşturabilir.
Veri Gizliliği İhlalleri: Bağlantılı araçlar, sürücüler, yolcular ve araç operasyonları hakkında hassas bilgiler de dahil olmak üzere büyük hacimlerde veri üretir ve iletir. Siber saldırılar yoluyla bu verilere yetkisiz erişim, gizlilik ihlallerine, kimlik hırsızlığına veya bireylerin hareketlerinin izinsiz takibine neden olabilir. Bir tehdit aktörü fikri mülkiyet (IP), ticari sırlar, finansal bilgiler veya kişisel olarak tanımlanabilir bilgiler (PII) gibi özel, gizli verilere yetkisiz erişim sağladığında bir veri ihlali meydana gelir. Veri ihlallerini içeren siber güvenlik vakaları en yaygın ve en pahalı vakalardır.
Siber Güvenlik ile ilgili Yasal ve Düzenleyici Uyumluluk İhlalleri: Yasa, yönetmelik veya endüstri standartlarının ihlaline yol açan siber tehditler ve saldırılar firmaların dava edilmesine ve para cezaları ödemesine yol açabilir.
Dolandırıcılık: Bir kişi veya kuruluş tarafından kişisel veya mali kazanç için kötü niyetle gerçekleştirilen kimlik hırsızlığı, kilometre sayacının kurcalanması ve hesap korsanlığı gibi aldatıcı eylemler korsanlar ve dolandırıcılar tarafından kullanılabilir
Elektrikli araç (EV) Şarj İstasyonları Güvenlik Açıkları: Bu güvenlik açıkları, şarj işlemlerini aksatmak, elektrik çalmak, kişisel verileri çalmak (Şarz Cihazları: kullanıcı kimlik bilgileri, şarj oturumu ayrıntıları ve konum bilgileri dahil olmak üzere hassas verileri toplar ve depolar), şarj ağının bütünlüğünü tehlikeye atmak veya şarj ağına yetkisiz erişim sağlamak için kötü niyetli kişiler tarafından potansiyel olarak kullanılabilir. Ayrıca elektrikli araç şarj altyapısında kullanılan bileşenler ve yazılımlar birden fazla tedarikçi ve üreticiden temin edilebilir. Bu bileşenlerdeki güvenlik açıkları veya tedarik zincirindeki tehlikeler, şarj altyapısına güvenlik riskleri getirebilir. Bunların yanı sıra Hizmet Reddi (DoS) saldırıları ile elektrikli araç şarj ağları, kötü niyetli aktörlerin ağı aşırı trafik veya taleplerle boğduğu ve şarj altyapısını meşru kullanıcılar için kullanılamaz hale getirdiği DoS saldırılarına maruz kalabilir.
Araçta Her Şeye Bağlı (V2X) Saldırıları: Araçtan her şeye bağlı (V2X), araçlara olanak sağlayan teknoloji için kullanılan ortak bir terimdir, altyapı ve diğer aktif yol kullanıcılarının sürekli iletişim halinde olmalarını sağlamak için mevcut hücresel ağ altyapısı olarak tanımlanabilir. Araç bağlantısının yedi temel modu vardır: Araçtan Altyapıya (V2I), Araçtan Araca (V2V), Araçtan Ağa (Trafik Işıklar vb. V2N), Araçtan Buluta (V2C), Araçtan Yayaya (V2P), Araçtan Cihaza (Şarz İstasyonu vb. V2D), Araçtan şehir elektrik şebekesine (V2G). Bu bağlantılara kullanarak yapılabilecek saldırılar emekleme aşamasındadır, ancak önümüzdeki yıllarda çok daha sık hale gelecektir.
Yukarıda belirtilen siber saldırılardan sonra yapılan yaygın olumsuz basın haberleri tüketici ve yatırımcı güvenini aşındırır ve kamuya açıklanan siber olayların finansal değerleme (piyasa değeri), güven ve algı üzerindeki olumsuz etkisi itibarın zedelenmesine neden olur. Ek olarak, bir aracın yazılım bileşenlerindeki siber güvenlik açıkları, üreticilerin sorunları güncellemek ve çözmek, etkilenen araçların güvenliğini ve düzgün çalışmasını sağlamak için geri çağırma yapmasını gerektirebilir ve bu da firmalar için çok büyük mali yükümlülükleri ortaya çıkmasına sebep olabilir.
Siber saldırılar Otomotiv, Akıllı Mobil Sistemler ve Hizmet Olarak Mobilite (MaaS) ekosisteminin her segmentini tehdit etmektedir:
1- Orijinal Ürün Üreticileri,
2- Yedek Parça Tedarikçileri
3- Araç Yazılım ve Donanım Tedarikçileri
4- Elektrikli araçlar
5- Elektrikli Şarj İstasyonları ve Elektrik Şebekesi
6- Otonom Araçlar
7- Tarım Makineleri
8- Mobil Nesnelerin İnterneti
9- Telematik Servis Sağlayıcılar
10- Filo Yönetimi
11- Araç Satış Bayileri
12- Araba, Ticari ve Teslimat Filoları
13- Toplu Taşıma ve Kamu Filoları
14- Acil Servisler
15- Araç ve Motor Paylaşım Platformları
16- Araç Kiralama Şirketleri
17- Araç Paylaşım Platformları
18- Akıllı Şehirler
19- Sigortacılık Firmaları
Bilgisayar Korsanları Karanlık ve Derin İnterneti kötü emelleri için kullanmaktadır, bunun yanı sıra profesyoneller ve kullanıcıların ana platformu haline gelen sosyal medya da tehdit aktörlerinin dakikalar içinde milyonlarca insana ulaşmasına olanak sağlamaktadır.
Üretken yapay zekâ, programcılar ve üreticiler için yeni olanaklar sağlarken, saldırı ortamlarını simüle etmek için Üretici Yapay Zeka kullanıldığında, daha öngörülemez ve sofistike saldırılara yol açtığı için siber güvenlik uzmanları ek bir zorlukla karşı karşıya kalmaktadır.
Son zamanlarda popüler olan ve önümüzdeki yıllarda daha çok yaygınlaşması beklenen otonom araçlar, teknik açıdan bakıldığında, yeni sensör türleri, yazılım ve donanım işlevleri, hizmetler ve iletişim türleri potansiyel güvenlik açıklarını ortaya çıkararak gelecekte bir saldırı olasılığını artırmaktadır. Otonom araçlar, internet ve uydular da dahil olmak üzere birden fazla kaynaktan veri ve yön alan navigasyon sensörleriyle (örneğin GPS, LIDAR, kameralar, milimetre dalga radarı, IMU) donatılmıştır ve bu yapılar önlem alınmazsa siber saldırılara karşı oldukça korumasızdır.
Örnek Olaylar:
Haziran 2023'te, önde gelen Tayvan merkezli bir yarı iletken üreticisi, bir fidye yazılımı grubu ve BT donanım tedarikçilerinden birinin dahil olduğu ve sistemin ilk kurulumu ve yapılandırmasıyla ilgili bilgilerin sızmasına yol açan bir siber güvenlik olayını kamuoyuna duyurdu. Saldırganlar, gizli bilgiler içeren dahili belgelere erişim elde ettiklerini iddia ederek, verilerin şifresini çözmek ve çevrimiçi olarak yayınlanmasını önlemek için 70 milyon dolarlık bir fidye talep ettiler- bu da tarihteki bilinen en büyük fidye talebi haline geldi. İhlal birden fazla otomotiv paydaşını etkileyebilecek olsa da şirket, tedarikçisindeki siber olaydan ne ticari faaliyetlerinin ne de müşteri bilgilerinin etkilendiğini bildirdi. Şirket ayrıca olayın ardından bu tedarikçiyle olan veri alışverişini derhal sonlandırdı.
Bir yıl önce, Amerika Birleşik Devletleri Wisconsin Eyaleti, Milwaukee şehrinde çoğunlukla Koreli bir araç firmasından yapılan araba hırsızlıklarında önemli bir artış görüldü ve şüpheli hırsızların çoğu araba kullanmak için çok gençti. Sosyal medyada, gençlerin bu arabalarla gezintiye çıktıklarını gösteren videolar ortaya çıktı- hız yapıyorlar, yoldan çıkıyorlar ve bazen camlardan sarkıyorlardı. Bu hırsızların amacı arabalardan parça söküp satmak değil, sosyal medyada nüfuz ve izlenme kazanmaktı. Araçların nasıl çalındığını gösteren videolar yayıldıkça, Koreli aracın hırsızlıkları ülke çapında arttı ve bunun üzerine Ocak 2023'te, Amerika'nın en büyük otomobil sigortacılarından ikisi, çalınması kolay bulunduğu belirlediği bu araçlar için belirli şehirlerde poliçe yazmayı reddetti.
Kaynak: 1-Açık İnternet Kaynakları
2- Upstream Global Automotive Cybersecurity Report 2024
Y STR KROMOZON İLE İLGİLİ YARGITAY KARARLARI (T.C. YARGITAY 2. Hukuk Dairesi Esas No: 2023/1719 Karar No: 2023/3075 Karar Tarihi: 07-06-2023) “Mahkemece yapılan yargılama sırasında Adli Tıp Kurumuna yazılan müzekkereye verilen cevabi yazı ile anne ve baba olduğu iddia edilen şahıslar olmaksızın, hangi cinsiyetten olursa olsun kardeş (aynı anne ve babadan) olduğu iddia edilen şahıslara ait biyolojik örneklerin çalışılması ile kardeşlik yönünde DNA incelemesi yapmak teknik olarak mümkün olmadığı, erkek cinsiyetli davalı ve davacılardan, Y STR DNA incelemesi ile bu şahısların aynı babasal soydan gelip gelmediklerine yönelik inceleme yapılması teknik olarak mümkün olduğunu, yapılacak bu değerlendirme babalık bir kardeş oldukları hakkında bilgi vermeyeceğini sadece erkek soyundan gelen erkek bireyler arasında aynı soydan geldiklerinin tespitinin yapılabileceğinin belirtilmesine dair müzekkere cevabı üzerine ... Büyükşehir Belediye Başkanlığı Mezarlıklar Daire Başkanlığı'na yazı yazılarak mezara ilişkin adres bilgilerinin istenildiği, ancak ... TC. Kimlik numaralı 24.02.1962 tarihinde vefat eden ...'ın defnedildiği mezara ilişkin herhangi bir kayda ulaşılamadığı, bu nedenle ... Adli Tıp Kurumu Başkanlığı'na yazı yazıldığı kardeşler arasında DNA incelemesi ile tarafların kardeş olup olmadığı hususunun sorulduğu, anne ve baba olduğu iddia edilen şahıslar olmaksızın, hangi cinsiyetten olursa olsun kardeş olduğu iddia edilen şahıslara ait biyolojik örneklerin çalışılması ile kardeşlik yönünde DNA incelemesi yapmanın teknik olarak mümkün olmadığı belirtilmiş, davacıların sunduğu nüfus kaydından ve salt tanık beyanları dikkate alınarak soybağı ilişkisi ispatlanamayacağından davanın reddine karar verilmiş, istinaf incelemesi neticesinde Bölge Adliye Mahkemesince istinaf başvurusunun esastan reddine karar verilmiştir. Nüfus kayıtlarının düzeltilmesi ve nüfus kayıtlarına yönelik tespit davaları kamu düzeni ile yakından ilgili bulunduğundan, hâkim istemle bağlı kalmayarak kendiliğinden de yapacağı araştırma ile elde edeceği sonuçlara göre karar vermek zorundadır. Somut olayda davalılardan bir kısmının Mahkemeye hitaben verdiği beyan dilekçesinde davacıların babası ile baba bir kardeş olduklarını beyan etmiş olmasına karşın Adli Tıp kurumunun cevabı yazısında belirtildiği şekilde erkek cinsiyetli davalı ve davacıların biyolojik örnekleri çalışılarak aynı baba soyundan geldiğinin tespiti için DNA tespiti yapılmaksızın ve davacıların nüfus kayıtlarında dedesi olarak görülen ve mezar yeri bilinen ...'a ait mezarda yapılacak fethi kabir sonucu alınacak örnekler ile davacılar ile kayıtta dedesi olarak bilinen kişinin gerçekten aynı soydan gelip gelmediklerinin tespiti ile tüm deliler birlikte değerlendirilerek sonucu uyarınca bir karar verilmesi gerekirken yazılı şekilde eksik inceleme ile karar verilmesi doğru olmayıp bozmayı gerektirmiştir.” (T.C. YARGITAY 8. Hukuk Dairesi Esas No: 2021/407 Karar No: 2021/4097 Karar Tarihi: 18-05-2021) “İddiaya dair DNA incelemesi yapılabilmesi için Şefaatli Asliye Hukuk Mahkemesi'ne talimat yazıldığı, talimat mahkemesince ... ile eşi ... ...'nın mezar yerlerinin tespiti için mahallinde keşif yapıldığı ve mezarların bulunduğu köyde 2000 ve 2010 yıllarında yaşanan sel felaketi sonrası mezarlığı da sel sularının bastığı ve mezar yerlerinin kaybolduğu ve ... ile eşi ... ...'nın mezar yerlerinin tespitinin mümkün olmadığının saptanması üzerine davacıların murisleri ... (...)'in, ..., ... ... ve ... ile ... ...(...), aynı anne babadan gelme kardeş olup olmadıkları, (otozomal STR DNA analiz çalışmaları ile mitokondriyel DNA analiz çalışması yapılmak suretiyle ), hususunda Adli Tıp Kurumu Biyoloji İhtisas Dairesince bu kişilerden alınan örnekler üzerinde çalışma yapılmış ve 26.09.2019 tarihli rapora göre; "Mitokondriyal DNA, sadece anneden çocuğa aktarılıp ve annesel soyağacındaki bireylerde (kardeşler, anneanne, teyze ve dayılar ile teyze çocukları gibi) aynı baz dizilimine sahip olduğundan, şahısların aynı annesel soydan gelip gelmedikleri ile ilgili bilgi sağlayabilir. İnceleme yapılan örneklerin mitokondriyal DNA'sının yüksek oranda polimorfizm gösteren HV1 bölgesindeki 16141-16521 arasındaki bazları / HV2 bölgesinin 31-400 arasındaki bazlarının yapılan incelemelerinde; ..., ... ..., ... ..., ... ve ...'ye ait mitokondriyal DNA dizilerinin birbiriyle uyumlu olduğu tespit edildi. Elde edilen sonuçlara göre ..., ... ..., ... ..., ... ve ...'nin aynı anne soyundan gelen bireyler olabileceği tespit edildi. ... ... ... Ve ...'ye ait YSTR DNA profillerinin birbiriyle uyumlu olduğu tespit edildi (Sadece erkek bireylere özgü olan Y kromozomu babadan oğula değişmeden aktarılır. Aynı soy ağacındaki erkek bireyler Y kromozomlarının mutasyona uğraması dışında aynı Y-STR DNA profiline sahiptir)” (T.C. YARGITAY 18. Hukuk Dairesi Esas No: 2015/1944 Karar No: 2015/15735 Karar Tarihi: 03-11-2015) “Dava Türk Medeni Kanunu'nun 301. ve devamı maddeleri uyarınca çocuk tarafından açılan babalığın tespitine ilişkindir. Mahkemece, davanın kamu düzenini ilgilendirmesi bakımından kuşku ve duraksamaya neden olmaksızın soybağının doğru olarak tespit edilmesi zorunludur. Öncelikle baba olduğu iddia edilen ………………’in mezarının tespit edilip fethi kabir yapılarak DNA incelemesine esas doku ve kemik örnekleri alınması, bu imkanın kullanılamaması halinde davacı ile kardeş olduğu iddia edilen davalılar arasında kardeşlik bağının olduğunu (aynı soydan geldiklerini) kanıtlar nitelikte DNA incelemesi yaptırılması ve alınacak rapor ile tarafların diğer delilleri birlikte değerlendirilip oluşacak sonuca göre bir karar verilmesi gerekirken eksik inceleme ve yerinde olmayan gerekçe ile davanın reddine karar verilmiş olması doğru görülmemiştir.” (T.C. YARGITAY 8. Hukuk Dairesi Esas No: 2018/16042 Karar No: 2020/928 Karar Tarihi: 05-02-2020) “Kamu düzeni ile yakından ilgili olan soybağının tespiti davalarında, Mahkemece, kuşku ve duraksamaya neden olmaksızın soybağının doğru olarak tespit edilmesi zorunludur. Öncelikle baba olduğu iddia edilen ...'ın mezarının tespit edilip fethi kabir yapılarak DNA incelemesine esas doku ve kemik örnekleri alınması, bu imkanın kullanılamaması halinde nüfus kaydına göre baba olduğu iddia edilen ... ile babalık bağı bulunan davalı ... ve davacı ... arasında baba yönünden kardeşlik bağının olduğunu (aynı soydan geldiklerini) kanıtlar nitelikte DNA incelemesi yaptırılması ve alınacak rapor ile tarafların diğer delilleri birlikte değerlendirilip oluşacak sonuca göre bir karar verilmesi gerekirken, DNA testi yaptırılmadan, nüfus kayıtlarına göre baba olduğu iddia edilen Havle ile davacının kardeş olduklarına dair rapor ve verilen tespit kararı ile davacı beyanları, bir kısım davalıların kabul beyanı ve tanık ifadeleri yeterli bulunarak davanın kabulüne karar verilmesi doğru görülmemiştir.” (T.C. YARGITAY 2. Hukuk Dairesi Esas No: 2023/6484 Karar No: 2023/5870 Karar Tarihi: 30-11-2023) “Nüfus kayıtlarının düzenli ve gerçeğe uygun olarak tutulması kamu düzeni ile yakından ilgilidir. Nüfus kayıtlarının düzeltilmesine ilişkin davalarda, mahkemelerin hiçbir kuşku ve duraksamaya neden olmaksızın doğru sicil oluşturmak zorunluluğu bulunmaktadır. Bu bakımdan hakim resen araştırma ilkesinin sonucu olarak kendiliğinden delil toplama yetkisine sahiptir. Mahkemece, bozma ilamı gereği annelik iddiası ile ilgili olarak DNA testi yapılması için ...'ın mezar yerinin tespit edilemediği, salt kolluk araştırması ve taraf beyanlarına göre yapılan tespitin nufüs kayıtlarının düzeltilmesine yeterli olmayacağı gerekçesi ile davanın reddine karar verilmiş ise de davacı vekili tarafından temyiz dilekçesi ekinde ...'ın mezar yerinin tespit edildiğine dair mezarlık ismi, mezar yerinin krokisi ve mezarlığın resmi sunulmuştur. Mahkemece belirtilen mezarın ...'a ait olup olmadığı yönünde tespit yapıldıktan sonra mezarda yapılacak fethi kabir sonucu alınacak örnekler ile DNA incelemesi yapılarak diğer tüm deliller birlikte değerlendirilip sonucuna göre karar verilmek üzere hükmün bozulması gerekmiştir.”
INTERPOL Kolluk Kuvvetlerini Uyarıyor: METAVERSE Suç Soruşturması Yöntemlerini Değiştirecek
Bölüm I
- Kolluk Tarafından Verilen Hizmetlerin ve İhbarların Metaverse Ortamında Yapılması
- Metaverse’de Olay Yerinin Korunması ve Adli Analizlerde Kullanımı
Bölüm II
- Meta Suçlar
Bölüm III
- Metaverse’de Adli Bilişim
Bölüm IV
- Metaverse Yönetimi ve Yönetişimi
Sonuç
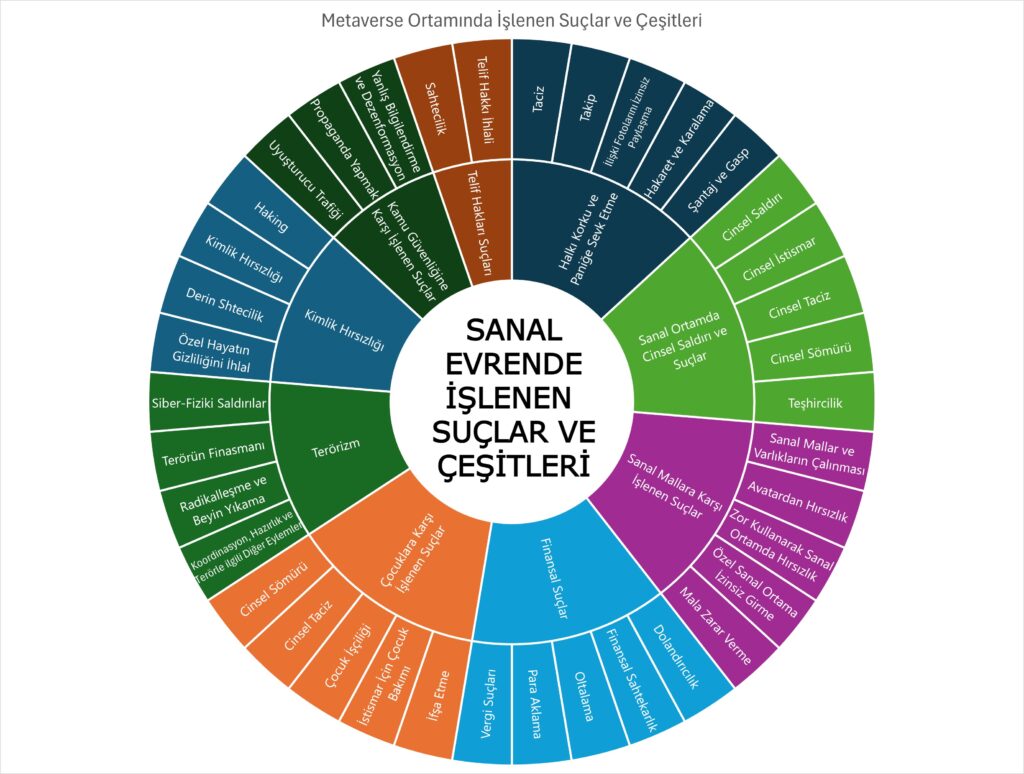
Sanal Evrendeki Suçların Tipolojisi
Mevcut suç ve zarar sınıflandırmalarının güncellenmesi ve uyumlu hale getirilmesi amacıyla aşağıdaki diyagram, Sanal evrende ortaya çıkan bazı suçların ve potansiyel zararların bir tipolojisini göstermektedir. Bu Meta suçlardan bazıları gerçek dünyaya kadar uzanabilir. Dünya Ekonomik Forumu, Sanal evrende’ ki zararların tıpkı fiziksel dünyada olduğu gibi yerel veya kültüre özgü olabileceğini vurgulamaktadır. Buna ek olarak, Sanal evren, özel bir yaklaşım gerektirecek jestler, duruşlar, dijital varlıklar gibi mekânsal zararları da ekleyecektir.
Kaynak: INTERPOL, GÜVENLİK KUVVETLERİ BAKIŞ AÇISINDAN METAVERSE, Vaka, Suç, Adli Bilişim, Soruşturma, Yönetişim, Ocak 2024, Bilgilendirici Belge
Adli Bilimlerin İlke, Prensip ve Kanunları
Mehmet ŞEN, Emekli Emniyet Müdürü, Olay Yeri İnceleme Uzmanı
Adli bilim, suç faaliyetlerinden veya hukuki veya idari davalardan kaynaklanan izleri incelemek için bilimsel bir süreç ve teknik yaklaşımlar uygulayan bir yöntemdir. Kriminalistik olarak da bilinen adli bilimler, hukuk mahkemelerinde ortaya çıkabilecek şüpheli sorulara yanıt bulmak için doğa bilimlerinin yasa ve ilkelerini kullanarak fiziksel kanıtların tanınması, belirlenmesi, bireyselleştirilmesi ve değerlendirilmesiyle ilgilenen bilimsel bir disiplindir. Adli bilimin bu ilkeleri, bir suçun ortaya çıkmasından sanığın mahkemede mahkûm edilmesine kadar olan ceza yargılamaları üzerinde doğrudan etkiye sahiptir.
Adli bilimin ceza yargılamasında önem taşıyan ilkeleri şunlardır:
________________________________________
1-Locard’ın Değişim Prensibi (Değişim Yasası)
Bu ilke Fransız bilim adamı Edmond Locard'a atfedilir. Teorileri, suçun önlenmesini ve toplumsal sonuçları birleştiren Kriminoloji, suç davranışının ve bunun hukuk sistemiyle olan etkileşimlerinin inceler. Adli bilimin temel ilkesini ortaya koyan adli bilim öncüsü ve kriminolog olan Locard: “Her temas bir iz bırakır.” sözü ile adli bilimin temel yasalarından birini belirlemiştir ve olay yerinde birçok iz kaldığını ve bunların uygun şekilde yorumlanması halinde en değerli bilgileri elde edilebileceğini öne sürmüştür.
“Herhangi iki nesne birbiriyle temas ettiğinde, aralarında her zaman çok küçük parçacıklar alışverişi olur”.
Bu prensibe göre, suçlunun veya suçun işlenmesinde kullandığı silahın mağdurla veya onun çevresi/nesneleriyle teması halinde o mahalde iz bırakabilmektedir. Aynı şekilde suçlu veya silahları da aynı temastan izler taşıyabilmektedir. Başka bir örnek olarak trafik kazasında çarpıp kaçma olayında çarpıp kaçan araçta kan lekelerinin varlığı söz konusudur. Aynı şekilde mağdurun üzerinde ve çevresinde de lastik izleri, ayakkabı izleri, araç boyaları bulunacaktır. Bir başka klasik örnek ise tecavüz mağdurunda bulunan kan/meni lekesi, zanlının vücudunda ise mağdurun saç varlığının görülmesidir.
Bu kanun bilimsel suç soruşturmasının temelini oluşturmaktadır. Bu prensip, parmak izleri, lastik izleri, atış artıkları, ayak izleri, saç örnekleri, cilt kalıntıları, kaslar, vücut sıvıları, kan, giysi parçaları vb. gibi temasın olduğu tüm durumlarda doğrulanır. DNA analizi bu prensibin basit bir uygulamasıdır ve analiz altında olan bulguların faile ait olduğuna inanılmaktadır.
2- Bireysellik Yasası
Bu ilke Paul L Kirk'e (1963) atfedilir ve adli bilimin yapı taşlarında biri olarak kabul edilir. Bu yasa, ister kişi ister nesne olsun, her varlığın benzersiz ve bireysel olduğunu ifade eder. Doğal ya da yapay hiçbir şey aynı olamaz. Tanrı'nın tohumlar, meyveler ve bitkiler gibi yarattıkları bile benzersizdir. Örnek: Banknotlar, madeni paralar, daktilo yazıları vb. aynı veya benzer görünmelerine rağmen benzersizdir.
Kirk, adli bilimin tek bir kaynaktan geldiği düşünülen iki öğenin (sorgulanan ve bilinen veya iz ve örnek) kaynağına odaklandığını iddia eder. Dolayısıyla kimliklendirme, iki şeyin aynılığından ziyade, olay yerinde bırakılan izlerden bireysellik oluşturmakla ilgilidir. Bu, izlerin ve örneklerin analiz edilmesi yoluyla tanımlamanın dolaylı olarak gösterilebileceği anlamına gelir; örneğin hiçbir iki parmak izi aynı değildir.
3- Sürekli Değişim Yasası
Sürekli değişim yasasına göre, “Zaman içerisinde her şey değişir. Yani kalıcı ve değişmez hiçbir şey yoktur.”
Sürekli değişim yasasının cezai soruşturma üzerindeki etkisi çok büyüktür. Suçlular zaman geçtikçe süregelen bir değişime maruz kalırlar. Suçlu zamanında yakalanmazsa; parmak izleri, kan lekelerinden alınan kan grupları ve DNA profili dışında kalan deliller ile ilgili tespit edilemez hale gelir. Ayrıca olay yerinde de hızlı bir değişim yaşanır, güvenliğin sağlanmaması durumunda olay yeri tespit edilemez hale gelir ve fiziksel delillerin kaybolması, tahrif edilmesi veya yok edilmesi ihtimali vardır.
4- Karşılaştırma Yasası
Farklı numuneler yalnızca benzer numunelerle karşılaştırılmalıdır. Başka bir deyişle, kan örnekleri diğer kan örnekleriyle, lifler de diğer liflerle karşılaştırılır ve bu böyle devam eder.
Karşılaştırma Yasası "yalnızca benzerlerin karşılaştırılabileceğini" belirtir. Veya “Karşılaştırma ancak benzer olduğunda mümkündür.”
Örneğin, olay yerinde bulunan bir kovan, ateşli silahla (tabanca) kıyaslanabilir ama pompalı tüfekle karşılaştırılamaz; Duvara yazılan yazı incelenirken kâğıt üzerindeki yazıyla değil, duvardaki benzer yazıyla karşılaştırılması gerekir. Bunun nedeni, herhangi bir kişinin kâğıda veya duvara yazdığında boyut ve hizalamaların değişebilmesidir.
5- Analiz Yasası
Analiz yasası, tahrifat ve imhayı önlemek amacıyla, analiz için doğru numunelerin öngörülen şekilde toplanması ve saklanması ile ilgilidir. Bunun nedeni, şüphesiz herhangi bir analizin kalitesinin, analiz altındaki numunenin kalitesine, delil teslim zincirine ve analistin uzmanlığına göre belirlenmesidir.
Bu ilke, “Analiz, numune analizinden daha iyi olamaz” veya “Analizin, uzmanlar tarafından doğru analiz yapılması için uygun numune alımı (doğru numune alma ve paketleme) ile yapılması gerekir” şeklinde ifade edilmektedir.
Örneğin: meni lekesi analizi durumunda, soruşturma memurunun kanlı elbiseleri toplamasının hiçbir faydası olmayacaktır. Patlayıcı maddenin test edilmesi gerektiğinde, patlama mahallinden toplanan ve patlamanın materyalist maddesini taşıyan artık malzemeler olmalıdır (patlayıcının kimliğini tespit etmek için tek başına toprağı test etmenin bir faydası olmayacaktır).
6-Olasılık Yasası
Tüm tespitler ve kimliklendirmeler bazen bilinçli ya da bilinçsiz olarak koşullara bağlı olarak doğrudur. Ayrıca adli analizden elde edilen sonuçlar, kullanılan yönteme ve bu yöntemin avantaj ve dezavantajlarına bağlıdır. Bunların dikkate alınması gerekir.
Bu ilke, "kesin veya belirsiz tüm tespitlerin bilinçli veya bilinçsiz olarak olasılığa dayalı olarak yapıldığı" gerçeğine dayanmaktadır.
Olasılık, belirli bir olayın, olayın gerçekleşebileceği çeşitli yollardan belirli bir şekilde meydana gelme şansını belirleyen matematiksel bir kavramdır. Örnek olarak burun hızması ve sağ kolunda dövme izi bulunan gözlüklü bir kadının cesedinin kimliğinin tespit edilmesi durumu verilebilir.
Sonuç olarak adli analiz, izlerin bulunmasına ve bunların bireylere bağlanmasına bağlıdır. Olay yerinde herhangi bir ize rastlanmaması durumunda şüphelilerin tespit edilmesi mümkün değildir. Ancak iz bulunması halinde, bunların uygun şekilde analiz edilmesi ve sonuçların uygun şekilde yorumlanması şartıyla delil olarak kullanılabilir.
7- İkinci Derece Gerçekler Kanunu
İlke şu ifadeye dayanmaktadır: "Gerçekler asla yalan söylemez, ancak insanlar yalan söyleyebilir."
Bu, görgü tanıklarının ifadeleri, mağdur ifadeleri vb. ile ilgilidir. İnsanlardan kanıt sunmaları istendiğinde, sundukları kanıtların hatalı olma ihtimali vardır. Bu kasıtsız (yanlış gözlemler yaparak, varsayımlarda bulunarak) veya kasıtlı (yalan söyleyerek veya abartarak) olabilir. Bunun aksine, gerçeklere ve delillere dayalı bir açıklama sunan (soruşturmaya dayalı) kanıtların doğru olma şansı daha yüksektir ve daha güvenilirdir.
Dolayısıyla Adli Bilim, ceza adaletinin idaresi amacıyla doğa bilimlerinin ilke ve yöntemlerini uygulayarak fiziksel delillerin elde edilmesine (tanımlanması), tespitine, bireyselleştirilmesine ve değerlendirilmesine yönelik bilimsel bir disiplindir.
Kaynak: https://simplyforensic.com/fundamentals-of-forensic-science/principles-of-forensic-science/
Why Is Quantum-Based Encryption Important to Protect Files Against Data Breach?
Without questioning the measures companies take to arm themselves against cybercrime, it is all too common for companies, despite all efforts made, to fall victim to malware and ransomware.
Thinking it won't happen to you because you employ or have hired the best cybersecurity specialist is a mistake many make. There is no 100% guarantee of cyber security because where people are involved, mistakes can be made. And small mistakes can have large consequences; in other words, security is only as good as its weakest link!
Of course, you can close and barricade all ports so no one can enter, but that usually has the consequence that working on the network entails the necessary inconveniences.
What you can do, is secure the data in such a way that cybercriminals cannot use it. Data they can't read is worthless to them. Exerting blackmail by threatening that your data will be exposed or sold to fellow criminals does not work if they cannot read any of your data and have no way of accessing the content. You may have been hacked and/or your system is being held hostage, but it is no more than, albeit slightly loaded, "an inconvenience" if your data is safe. There is no risk of data breaches or blackmail pressure, as there is no big deal to negotiate for these cyber criminals.
So, how do you secure your data? At least not with the usual encryption methods, because they will no longer hold up with the advent of quantum computers. With a quantum computer, encrypted files are decrypted in no time and then you nevertheless are screwed.
How to secure and why?
You better consider quantum-secure encryption because, as mentioned, quantum computers have the potential to break through traditional encryption methods. And that was precisely the solution to secure confidential data and communication, was it?
Quantum computers use a different computer architecture than classical computers, allowing them to factor large numbers exponentially faster than classical computers. Quantum computers can break through traditional encryption algorithms such as RSA or elliptic curve cryptography with the greatest ease.
That is why we offer our solution with encryption algorithms to address the potential threat of quantum computers. These algorithms are designed to be guaranteed to be secure against attacks from both classical and quantum computers and several combined techniques are used to encrypt data. For example, you can think of grid-based cryptography or hash-based cryptography.
By implementing quantum-safe encryption, you can ensure that your sensitive data is 100% protected, even if it comes into the hands of cybercriminals using a quantum computer.
The DBV Quantum-Safe Data Encryption provides a four-layer encryption, consisting of a combination of different encryption techniques.
Each encryption system is configured custom-made, so only you can decrypt your data with a self-created “passphrase”. No keys are stored; not on the workstation and not on the network.
It takes only a few milliseconds to generate a key. After that, it disappears and cannot be found by anyone. Files can only be unlocked with your own passphrase.
So what can you encrypt? Well, everything from texts and files to complete databases.
Interested to learn more?
It’s our pleasure to explain more about our quantum-safe solution. Please visit our website and leave us a message with your contact details or call us to schedule a video chat. And of course, this will be without any obligation.
Türkiye Contact https://siriuskriminal.com/iletisim/
Sirius Kriminal signed a dealership agreement with DFEND [Tech for Secure World] regarding the quantum-based encryption system.
Sirius Criminal signed dealership agreement with Systool Company, which provides world-class, robust and affordable solution services with a focus on guaranteed data security, high data quality recovery, migration to the Cloud and digital forensic solutions and software.
CYBER SECURITY (SUMMARY)
ADVANCE THREAT PROTECTION
- Botnet Protection
- Malware Analysis and Anti-Malware Saolutions
- Sandboxing and Emulation
- Application Whitelisting
- Network Forensic
- Automated Security Analytics
RISK GOVERNANCE AND COMPLIANCE
- ISO 27001 / HIPAA / PCI & SOC
- Firewall Compliance and Managemen
- Configuration Compliance
- Audit and Compliance Analysis
NETWORK SECURITY
- Firewall Management
- Network Access Control
- Secure Network Design
- Unified Thread Management
- Remote Access Solutions
- Intrusion Detection and Prevention System
- Pentest
INFRASTRUCTURE SECURITY
- DNS Security
- Mail Security
- Unified Communication
- Security Information and Event Management (SIEM)
- Zero Day Vulnerability Tracking
- Logs and False Positive Analysis
APPLICATION SECURITY
- Web Application Security
- OWASP Top 10 and SANS CWE Top 25
- Database Activity Monitoring
- Content Security
- Secure File Transfer
- Web Application Firewall
- Secure Coding Practices
- Testing for Vulnerability Validation
- Application Pentest
- Secure Code Review
SYSTEM SECURITY
- Windows / Linux Server Security
- Vulnerability / Patch Management
- Automated Vulnerability Scanning
DATA SECURITY
- Data Encryption
- Data Leakage Prevention
MOBILE SECURITY
- Authentication and Onboarding
- Rogue Access Point Detection
- Wireless Security Protocols
- OWASP Mobile Top 10
- Mobile App Automated Scanning
- Dynamic Mobile App Analysis
- Secure Coding Practices
- Mobile Pentest
- Secure Code Review





The second of the Kosovo Turkey Forensic Sciences Days, the first of which was held in Prizren-Kosovo in 2014 was held in Foça-İzmir on 25/26 April. We took part in the event with our presentation "Identification of Disaster Victims in Afghanistan Plane Crash and Kosovo Mass Graves".
Polislikle ilgili Kitap Kataloğu 1- Practical Crime Scene Investigations for Hot Zones; J.T.Fish, R.N.Stout, E.W.Wallace; Practical aspects of criminal and forensic investigations series; CRC Press; Taylor&Francis Group 2- Emergency Response Handbook for Chemical and Biological Agents and Weapons; John R. Cashman; CRC Press; Taylor&Francis Group 3- Women Who Sexually Abuse Children; Hannah Ford; NSPCC 4- The Explanation of Crime; Context, mechanisms and development, Cambridge edited by Per Olaf W. Wikstrom and Robert J. Sampson 5- The Information Security Dictionary Defining the Terms that Define Security for E-Business, Internet, Information and Wireless Technology; Urs E. Gattiker; Kluwer Academic Publishers 6- Terrorism and Organised Hate Crimes; Intelligence gathering, analysis and investigatios; Michael R. Ronczkowski; CRC Press 7- Techniques of the Professional Pickpocket; Wayne B. Yeager 8- Sexual Murder; Catathymic and Compulsive Homicides, Louis B. Schlesinger; CRC Press 9- Serial Offenders, Current Thought, Recent Findings; Edited by Louis B. Schlesinger, Ph.D. ; CRC Press 10- The Human Skeleton in Forensic Medicine; Third Edition; Mehmet Yaşar İşçan, Maryna Steyn 11- Manual of Forensic Odontology; Edited by David R. Senn 12- Adli Bilimlerin Temeli; Mea M. Houck, Jay A. Siegel, Çeviri Editörü Yeşim Doğan 13- Advances in Forensic Human Identification; Edited by Xanthe Mallett, Teri Blythe, Rachel Berry 14- Adli Dil Bilimi; Editörler Prof. Dr. Selma Elyıldırım, Prof. Dr. İsmail Hamit Hancı, Seçkin Yaınları 15- Crime Scene Analysis and Reconsruction; Ross M. Gardner, Tom Bevel 16- Cadavar Dog Handbook; Forensic training and tactics for the recovery of human remains; Andrew Rebmann, Edward David, Marcella H. Song 17- Crime Scene Reconstruction; W. Jerry Chisum, Brent E. Turvey
DNA Phonetyping
By comparing samples, DNA collected at a crime scene can be matched to a suspect as well as used to identify what a suspect looks like physically. Forensic scientistcan sequence a DNA sample and give investigators information about the suspect's distinguishing characteristics such as hair, eye, skin colour, age and biological backround.
Immunochromatography
Immunochromatography tests are used in forensics to detect drugs and pharmeceuticals in a subject’s bodily fluids. A smartphone-based sensor has even been developed to perform immunochromatography on a saliva without the requirement for a lab visit.
Geolocoting a suspect or victim using stable isotopes of water.
Scientist can pinpoint where a sample came from by isolating the isotopes in a water sample found on a suspect or victim, according to recent findings. If there are enough samples, the isotopes can even reconstruct the subject’s route. Other methods of isotopes detection can be used to ascertain the number of persons present.
Dijital araç adli bilimler
Dijital araç adli bilimler bir araç sisteminden dijital verilerin (dijital kanıt) tespit edilmesi ve analizi; dijital araç adli bilim araştırması olarak adlandırılır. Bu bilgiler, araçların karıştığı kazalar, hırsızlık, dolandırıcılık ve araçların dahil olduğu cezai davranışlarla ilgili davalarda çalışan hukuk ve cezai soruşturmacıları için yararlı bilgiler sağlayabilir.
Digital surveillance for XBOX (XFT device)
Most people do not think of a gaming system as possible spot to store illegal data, which is why criminals have become so reliant on them. The XFT is being created to give authorities visual Access to hidden files on the XBOX hard drive, making it one of the most groundbreaking forensic Technologies for digital forensic specialist
